
The Internet of Things (IoT) is one of the fastest growing technological revolutions the world has ever seen, with billions of devices connected in homes, smart factories, offices and even in remote locations.
Yet, as the IoT proliferates, so do the potential access points for the security risks posed by malicious attackers. In many ways, as machine-to-machine (M2M) communication is central to the IoT, these attacks are far more significant than ‘normal’ computer attacks as actual physical machines can be taken over.
In this article, Infineon Technologies and EBV will look at some of the implications of security breaches and consider how designers should approach the task of planning and implementing a secured IoT infrastructure. The article will look at how hardware-based security has a pivotal role to play as well as some services – particularly the device personalisation service by EBV – that significantly ease the deployment of hardware-based security solutions.
The need for IoT security
There are a huge number of businesses basing part or all of their future prosperity on the myriad of applications that use cloud services and artificial intelligence to deliver revenue streams. In fact, Cisco recently estimated that in the next five years this business sector will add some $19 trillion to global GDP.
The billions of connected devices that are already deployed are key enablers of this significant new sector of the economy. And, while their connected nature allows them to deliver value, it also exposes them to the possibility of malicious attacks that could result in intellectual property theft, stolen personal information, interruption of business operations and even endangering a company’s brand image and, ultimately, its existence.
The threat is very real and global, affecting many large organisations, both commercial and government. More damaging than simple computer viruses, as many IoT devices are directly connected to machinery and infrastructure, attacks on IoT infrastructure have reportedly led to the shutting down of steel plants, power stations, major businesses and even a nuclear facility. At the consumer level, Incontrol reported that 71% of consumers fear that their personal information may be stolen, which is clearly slowing the adoption rate of this new technology.
As fast as new IoT technology is being developed, the ‘bad guys’ are developing ever more sophisticated ways of compromising the security measures. Popular methods include physically microprobing the ICs, analysing electromagnetic emission, inducing faults in operation by power supply manipulation or through adding clock glitches.
IoT security for designers
In order to be properly protected, security is needed in all aspects of the system, covering the application, communications to/from the device and also within the physical device itself. Properly executed (Figure 1), this approach will protect confidentiality, integrity and availability.
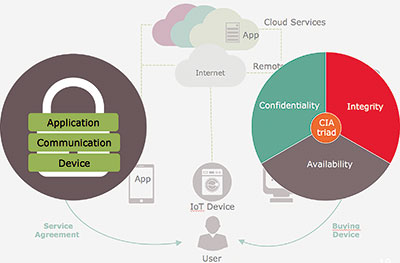
The first step for any designer is to consider what levels and types of security are appropriate for the task at hand. The nature of the target and its value are important considerations, as is brainstorming possible attack methods, the likelihood of such attacks and the impact of any successful attack.
Having weighed up these factors the designer will then go on to consider how attacks can be avoided and the costs of doing so, as well as any impact the measures will have on overall system performance and maintenance.
Given their nature, IoT devices have some specific needs and challenges where security is concerned (Figure 2). Generally speaking, IoT devices have limited MCU and memory resources and utilise non-rich operating systems, so security devices must support these embedded OS and work within the small host memory footprint. Physically, IoT devices are small and this must be mirrored in the chosen security solution.
Many IoT devices are powered by coin cells or energy harvesting techniques, so the security devices must be extremely frugal with their energy usage, as well as offering a low cost to align with the cost sensitivity of most IoT devices.
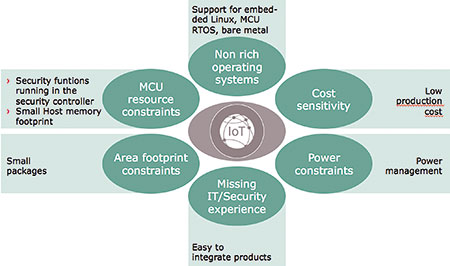
Finally, many IoT designers are not experts (or even experienced) in security, so the chosen solution must be easy to implement. More often than not this means selecting a supplier with an extensive support infrastructure available, both directly and through technically competent channels of distribution.
Hardware is an essential ingredient
While software and encryption can provide a level of security, there are some notable weaknesses to a software-only approach. For example, during the process of authenticating an IoT node (Figure 3), certificates and public / private keys are exchanged and processed to ensure the recipient device is properly identified and authorised. However, in a software-only system this can mean moving the private key into non-secure memory to allow processing to be performed. This exposes the private key to malicious attackers, thereby compromising the overall security of the system.
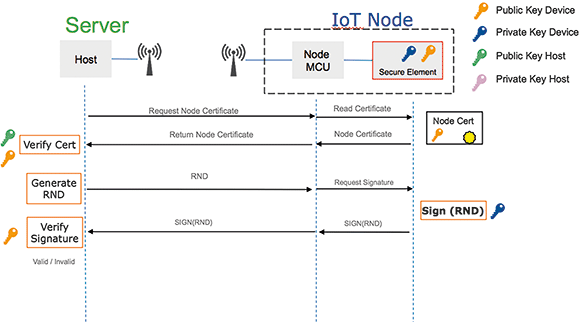
Hardware-based security solutions, such as the OPTIGA Trust X from Infineon Technologies, operate as a secure element. This means that the private key is processed only inside the secure element, thereby protecting the private key from being discovered and guarding system security from being compromised.
OPTIGA Trust X is a fully featured device security solution that offers premium-grade security based on a CC EAL 6+ (high) certified security controller that supports TLS/DTLS and X.509 certificates. It is TRNG AIS-31 certified and supports USB Type-C authentication as well as providing a cryptographic toolbox that allows flexible customisation.
The ability to customise and tailor OPTIGA Trust X allows it to be used in an extensive set of use cases including mutual authentication, secured communication, data store protection, lifecycle management, power management and the all-important secured updates that keep IoT devices bug-free and up-to-date.
Despite the power of OPTIGA Trust X, the turnkey solution is easy to integrate into IoT applications. Infineon provides all necessary host code, a customer specific public key system, an evaluation kit and a wealth of knowledge and expertise that is made available to designers.
Device personalisation
Adding a secure element to a design and making use of its authentication or encryption features is only one aspect. Since crypto keys are the heart of any security measures they have to be generated in a secure way and in an area where only authorised people have access. Furthermore, certificates have to be generated and signed with a private key which must never leave the HSM (hardware security module). All these requirements demand a significant investment in terms of time, knowledge and equipment.
This is where EBV can help customers with their personalisation service under its ‘Secure-it’ brand. Along with a highly trained and experienced technical support team, EBV is able to offload the customer from the programming effort. Through the service, the company can offer the generation of certificates as well as the creation and programming of security keys, delivering customer specific devices for IoT applications in an easy way (Figure 4).
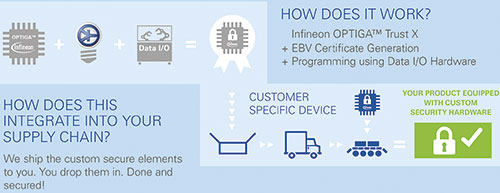
The programming is carried out using data I/O hardware that is held in a physically secured environment and housed in a fenced area at EBV’s facilities in Germany. None of the equipment is connected to the Internet and, therefore, is not susceptible to any form of attack or malicious tampering – protecting all devices programmed by EBV.
The service fully integrates into existing customer supply chains and the ordering process is identical to that used for standard parts. While EBV has the capacity to program volume shipments, it also caters for lower volumes which is useful for specialist applications or for prototype runs of new products. The simple-to-use service saves customers from having to develop in-house security procedures to protect keys and also removes the need for investment in programming hardware, giving access to a flexible programming service for minimal investment.
Summary
Protecting all aspects of an IoT system is essential, as is tailoring the security approach and levels to the value of the application and the probability of an attack happening. While software and encryption go some way towards offering security, a hardware-based security approach is a far stronger solution.
Infineon’s OPTIGA Trust X is a fully featured turnkey security solution for IoT devices that meets the many and somewhat challenging needs for deploying security in an IoT environment. Included in the support ecosystem is a high level of support as well as the device personalisation service from Infineon’s trusted partner, EBV.
For more information contact EBV Electrolink, +27 21 402 1940, [email protected], www.ebv.com
| Tel: | +27 11 236 1900 |
| Email: | [email protected] |
| www: | www.ebv.com |
| Articles: | More information and articles about EBV Electrolink |

© Technews Publishing (Pty) Ltd | All Rights Reserved