
Centralised control systems have a single controller directly attached to input and output devices - the most common implementation of a control system found in industry. Centralised controllers act upon the state of the various input devices and setpoints by manipulating outputs to achieve the desired result. Devices such as transmitters and actuators, located in the field, would be connected to signal conditioning electronics located at the centralised controller.
A common method of connecting these field devices to the centralised controller is by utilising a 4-20 mA current loop, which is an industry standard. Here, each field device would be powered from a single loop power supply (typically 24 V d.c.). For transmitters, the value of the current indicates the parameter value being measured such as temperature. For actuators, the current value represents the value of the command signal such as valve position. There are numerous advantages to using the 4-20 mA standard. On most devices, the current actually powers the device, thereby requiring only two wires. Since it is only current being measured, a voltage drop in the field wiring due to long distances does not introduce measurement error.
Although effective, the 4-20 mA scheme has one major drawback; field wiring can be excessive since a minimum of one wire must be dedicated per field point to the centralised controller. It is this issue plus others that sparked the movement towards a unified fieldbus.
The fieldbus concept
The term 'fieldbus' means the attachment of field devices over one bus connection. A bus connection means that multiple devices can share the same set of wires so instead of having one wire dedicated to one device, a fieldbus would allow multiple devices to be attached over one or more wires. Reduced wiring is only one of the goals of having a fieldbus. This bus would not be an analog connection like 4-20 mA, but a digital connection where digital data would represent the process signals sent over the bus. By having all devices on a single connection, a means must be provided to 'address' each device since only one device can have access to the bus at any one time. Otherwise, there would be conflicts. Once devices are addressed, much information can be gained by communicating with the device. For example, not only would the value of the process signal be sent but information about the device itself. This data could consist of the instrument tag number, the model number and the calibration data. Instead of sending process data representing a 4-20 mA signal, which is of little use if one does not know the instrument's scaling, why not just send the data in engineering units such as 310°C? There are benefits to sending process data over a fieldbus. The fieldbus topic is part of the field of industrial networking.
Topology
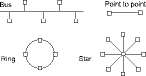
Topology refers to the physical arrangement of devices that are connected to one another (Figure 1). The simplest of connections is the point-to-point connection where only two devices are connected together. A controller connected to a transmitter is an example of a point-to-point connection. However, if you consider a centralised controller connected to several transmitters and actuators, this would be an example of a star topology. The centralised controller is the centre of the star. The purpose of a fieldbus is to have all field devices connected as a bus in order to minimise field wiring. A bus connection allows several devices to share the same wires which is called bus topology. The final topology that will be introduced is the ring topology which is simply a circle with devices occupying positions along the ring. There is no 'best' topology. All are effectively implemented in industrial networking systems. Topology mainly depends upon the communication method which will be discussed next.
Simple communication
An example of 'simplex transmission' could be a baby-monitor, since only the baby initiates a transmission. The parent is always the receiver. The communication is thus only one way. On a two-station intercom, a user presses a button (push-to-talk) and calls up another person. If the person answers the call, they each communicate by pushing a button. This is called half-duplex operation since communication is two ways but only one can talk at a time. If it were possible to talk both ways at the same time (intelligently), then this would be called full-duplex operation.
If the intercom system were to include identical stations in every room, (Figure 2), we would say that stations are peers since there is no hierarchical structure of one station having more capability than another. We call this peer-to-peer communication. Each station has the same push-to-talk button, and there are no restrictions on station use. When a caller initiates a transmission, the button on the originating station is pressed and all other stations will hear the transmission. This type of transmission is called a broadcast since all stations receive the message. If the message is 'come to dinner,' and directed to all parties, then this type of transmission is effective.
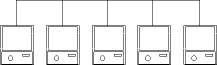
If the transmission were to be directed to only one person, then a protocol would need to be developed in order to have a meaningful conversation. A protocol would be a set of rules that would govern communication. By following the same convention, communication efficiency is achieved. Assume a mother wants to know if daughter wants to go shopping. Mother would initiate a transmission requesting that daughter come to nearest intercom and acknowledge receipt. This is an example of a unicast or directed transmission since only two stations are participating. This is also called establishing a connection. Mother would wait a certain amount of time for a response. If none is received, mother will retry for a certain amount of time before abandoning the attempt. If daughter does answer, mother can then state her business. If daughter does not understand the question, she would request a re-transmission. Once all the information is transferred and acknowledged and a plausible response obtained, the two cease communicating and the connection is terminated. The system is now available for others to use. Since the system must be shared, the protocol requires that others must wait if the system is busy.
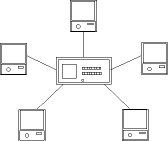
Another popular intercom system would have one master station and several remote stations (Figure 3). The master can communicate to one or more remotes, but a remote can only call the master. This configuration would be a star topology and the communication is half-duplex. The master has the ability to select just one remote for a unicast transmission, select several remotes for a multicast transmission or all remotes for a broadcast transmission. The remotes do not have this same capability so this configuration is a hierarchical system because the master has more ability than the slaves.
In industrial networking we have inanimate objects communicating data between stations. To better visualise the interactions between devices, we use a communication model. This model is helpful in comprehending industrial networking principles.
OSI model
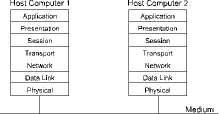
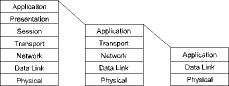
When focusing on industrial networks, it is very helpful to refer to the open systems interconnect (OSI) Reference Model, which was published by the International Organisation of Standards (ISO). The OSI model describes seven layers as they relate to one host computer communicating to another host computer (Figure 4). Not all host-to-host communication must go through all seven layers, but it helps to note what layers may be affected. Here are the seven layers:
* Physical layer: This is the lowest layer which describes the way actual data, in the form of symbols, are sent over a medium such as copper wire or fibre-optic cabling. Items like signal levels, symbol representation and connector pinouts are defined at this layer.
* Data link layer: The data link maintains a reliable connection between adjacent nodes or stations over a physical channel. To distinguish one node from another, a method of node addressing must be defined. To ensure only one node has access at any one time, a method of medium access control (MAC) must be implemented. Information sent over the data link is called frames.
* Network layer: A network layer is required when communication must span multiple networks. This is called internetworking, and the most famous internetworking protocol is called IP - the Internet Protocol. If communication is confined to just one network, this layer is not required. Data sent over the network layer are termed packets.
* Transport layer: This layer is concerned with the reliable transmission of messages sent between two host computers. This is different from the data link layer which is only concerned with the transmission of frames. A message usually requires many frames to be sent before the complete message can be received. This requires fragmenting the message into many pieces to be reassembled at the other end. Missing fragments must be resent. The transport layer addresses this issue.
* Session layer: The session layer is concerned with the establishment and termination of communication sessions between processes in host computers.
* Presentation layer: The presentation layer translates the format of data between sender and receiver.
* Application layer: The application layer represents the user application. This could be electronic mail for example.
The seven-layer OSI model is useful for discussion purposes, but is often too complex for all network architectures. For example, the functionality of the presentation and session layers can be included in the application layer with little loss of clarity. When discussing protocols that power the Internet, this is frequently done. The seven-layer model is reduced to a five-layer model when discussing the Internet (Figure 5). Since many industrial networks do not expand beyond one network, the network layer is unnecessary, and it is possible to include the transport layer with the application layer. Now the OSI model is down to a minimum of three layers. Three layers are plenty to talk about so we will only address one aspect of the data link layer which is important to understand and that is medium access control (MAC).
Medium access control
In a fieldbus or industrial network, several stations share the same communication media in order to save wiring costs. However, since the medium is shared, not all devices can communicate simultaneously. Therefore, there must be rules to govern who gains access to the medium and those rules are called medium access control.
There are several MAC implementations, but they basically fall into two main categories: CSMA/CD and token-passing. We will discuss these two methods, again using analogies:
* Carrier sense, multiple Access (CSMA): Probably the most popular method of gaining access to a network is the carrier sense, multiple access method. This method is very similar to human conversations among several people. Assume for the moment that we have been instructed to join a telephone conference call (multiple access) at 10:00 a.m. At the appointed time we make the call and hear conversations occurring. Being polite, we do not break into the conversation (defer) until we hear silence (lack of carrier). Once we determine an opportunity to speak, we announce our name to all other participants (broadcast). The other participants may log our name onto a piece of paper in an attempt to visualise everyone on the call.
Anyone who has participated on a conference call with several other people can appreciate the difficulty of communicating without seeing each individual. Once the channel is clear, you begin to talk, first by identifying yourself and then by identifying the person you want the message to go to. If it is only one person, it is called a directed or unicast message. If it is to a group of people, it is called a multicast message. If it is to all people, it is called a broadcast message. Now let us assume that after hearing silence, you begin speaking and you notice someone else is speaking as well. This is called a collision. Since you were able to notice the collision by listening, we call this collision detection (CD). After both you and the other person notice the collision, you both back off from speaking for a random amount of time. Usually someone is more patient than the other, so one person will try again to speak. If no more collisions, this person will acquire the channel and send his/her message. The other person will wait (defer) until the channel is again clear and will again attempt to acquire the channel. This type of medium access control is very common and is the basis for shared Ethernet.
* Token-passing protocol: A much different approach to resolving medium access is called the token-passing protocol. With this approach, each participant to the network is guaranteed some time to transmit a message on a permission basis. This permission occurs when a participant receives the one token that exists in the network. The token is passed from one participant to another in a circular fashion in what is called a logical ring. Once a participant receives the token, the participant must initiate a transmission or pass the token to the next participant in an orderly fashion. Usually each participant is assigned a number representing his or her node or station address. The token is usually passed from one participant to another with the next highest address regardless of the next participant's physical location. The participant with the highest address will pass the token to a participant with the lowest address. It is not necessary to have one master or a facilitator to hand out a token. Participants could be peers to one another and simply agree that they will not possess the token for more time than previously agreed.
For a simple example of how this works, assume a family of four - mother, father, daughter and son - sitting down together for dinner. Dad has just come home from work and everyone is anxious to discuss the issues of the day with dad. In order to eliminate the chaos of multiple, simultaneous outbursts at the dinner table, the family agrees to a simple set of rules. The person in possession of the salt shaker has momentary sole right to initiate a message. Messages will be restricted to a maximum length in order to reduce hogging. Once a message is completed, the salt shaker must be passed to the left. Daughter is first to have the salt shaker (token) and initiates a transmission to dad informing him that she just received a very high grade on a test. Dad does not respond since he does not have the token. Instead son receives the token from daughter and informs dad that his favorite baseball player has been traded. Dad receives the token and congratulates daughter on a fine achievement. He would like to respond to his son but he can only initiate one directed message, to daughter in this case, for each token pass. Dad passes the token to mom. Mom informs dad that the washing machine has suddenly and mysteriously stopped with an intense grinding noise. The token is then passed to daughter who has nothing to say and simply passes the token to son. Son announces to everyone at the table (broadcast message) that he will soon have his driver's permit. The token is passed to dad, who ignores son's first message and second and enquires of Mom, "What noise?"
The token-passing protocol has several benefits. First, all participants have equal access to the network making them all true peers to one another. Second, network collisions are avoided by restricting a transmission to one and only one participant. Finally, the maximum amount of time required for a participant to gain the token and initiate a transmission can be determined by knowing the protocol and by knowing the number of participants. That is why a token-passing protocol is referred to as a deterministic protocol. This can be important in industrial networks when events must occur in a timely manner. Examples of networks that use the token-passing scheme include ARCNET, ControlNet and Profibus.
Summary
We have begun understanding the basics of industrial networks by using analogies of human interactions. However, industrial networks involve inanimate objects communicating data in a defined fashion.
For further information contact Contemporary Controls' representative, Electronic Products Design, (012) 665 9700.

© Technews Publishing (Pty) Ltd | All Rights Reserved