
After decades of improvements in satellite-based timing and positioning accuracy, market expectations are moving towards increased robustness and security. Our response: the u-blox M9 and u-blox F9 platforms.
Back in 2016, global navigation satellite system (GNSS) receivers were being spoofed by an unexpected cohort of users: Pokémon Go players. By tricking their smartphones into believing that they were moving around, these players had found a way to win points – and online prestige – without even getting off their seats. Even though it posed little threat, the story made headlines. If kids could so easily spoof a GNSS receiver to cheat on a computer game, well, so could anyone else. It wasn’t news, but now it was clearer than ever: satellite-based positioning had a security problem.
Fortunately, it was a security problem that left most end users unaffected. But as GNSS receivers are relied on in a growing number of business- and mission-critical use cases, e.g. to synchronise cellular base station networks and smart grids, enable pay-for-use road tolling, or track vehicle fleets, finding ways to subvert them has become a business of its own, with significant financial rewards for the spoofers and economic consequences for the spoofed. It is, therefore, no surprise that customer focus is shifting from accuracy – a problem that has largely been solved – to increased robustness and security.
A vast threat space
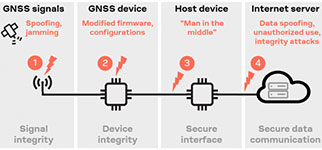
A GNSS receiver’s position and timing output can only be as good as the signals it receives at the antenna. Unfortunately, jamming and spoofing receivers has never been so easy. RF jammers – available online – can drown out weak GNSS signals in a sea of noise, interrupting service. It’s a strategy fishing vessels have used to hide illegal expeditions into protected waters. Uber drivers on the way to lucrative locations such as airports have used GNSS spoofers to get to the front of the queue by making it look like they were already there. And the list of scenarios goes on...
The GNSS receiver itself presents a second vulnerability. Many commercial drones are programmed not to take off in or fly into no-fly zones. By breaking into the GNSS receiver’s firmware, these restrictions can potentially be removed. But that isn’t all. Malicious users can change other device configurations, e.g. via the debugging interface, to circumvent legal restrictions or deliberately manipulate receiver performance, modify the firmware, or access sensitive data.
And finally, time and position data determined by the receiver can be spoofed during transmission in a man-in-the-middle attack, either on its way from the GNSS receiver to a host device, or from the host device to the cloud. This threatens data confidentiality and integrity, as the data can be sniffed to extract sensitive information or replaced by false data.
u-blox M9 and F9 tackle each of these attack surfaces
Robustness and security were front and centre on our minds in developing u-blox M9 standard precision and u-blox F9 high precision positioning platforms. Leveraging advances in GNSS satellite signals, RF signal processing, embedded software development and data encryption, u-blox M9 and F9 tackle GNSS security from the antenna all the way up to the cloud.
By concurrently tracking multiple GNSS constellations across a wider range of frequency bands, our u-blox M9 and F9 receivers increase the level of sophistication required to spoof unnoticed. Consistency checks between the various inputs help catch spoofing attempts. And improved hardware and software filtering help mitigate unwanted in- and out-of-band interference to improve GNSS performance.
To ensure that the GNSS receiver’s firmware is not tampered with, a secure boot procedure validates firmware images at boot time so that only original firmware runs on the device. An irreversible configuration lock protects devices from being doctored once deployed. And, finally, host message authentication secures the interface between the GNSS receiver and the host, while SSL/TLS protects data as it is sent from the host to the cloud.
With the many security features they offer, u-blox M9 and F9 GNSS receivers are designed to fend off a variety of malicious attacks on mass market compatible GNSS solutions. But as the truism goes: there is no such thing as 100% security. Investing in trusted positioning technology is a vital step towards closing in on the 100% mark. But it is only one step in a broader process.
Optimising security requires considering security across all aspects of the product’s development and deploying, from sourcing and design to implementation and operation. It comes at a cost. But regardless of the use case you are targeting, with robustness and security moving from being a differentiator to a minimum requirement, being ahead of competition today will pay off in the long run.

© Technews Publishing (Pty) Ltd | All Rights Reserved